Consumers Value Sharing. Security Will No Longer Stand in Their Way.
Rethink consumer access management.
“Read this.”
We’ve all done it: Shared an article and then shared our password, because the person we sent the article to, couldn’t access it.
We do it in our professional life — with colleagues — and in our personal life — with family or friends.

Media companies look for ways to prevent this habit of sharing passwords by offering attractive group or family subscriptions or by trying to detect freeloading, which most of the time only works when two people are logged in at the same time with the same credentials.
Our view is that you shouldn’t try to prevent sharing. Instead, you should promote it, albeit in a secure way.
You Might Like This
Imagine if a media company could publish a “share this article” link where all you need to do is enter the email address of the person you want to share the article with. That person then gets an email asking him or her to sign up to read the article that you’re recommending.
Sounds simple, right? Well, not really, because practically no access policy includes relationships as a condition to get access. Everybody is familiar with granting permissions based on roles — a manager can do this — or purchases — a person with a subscription can view that.
You only get one chance to make a good first impression, and yours may be in the hands of advanced access management.
Relationship-based access control lets companies add relationships as an attribute to grant access, as in, if the person I invited is my friend, he or she can get access to that article.
Lots of industry verticals can benefit from consumer-directed access, where the consumer is firmly in the driver’s seat to share the access he or she has.
When a consumer has to choose a service that is expensive or that poses the risk of significant emotional consequences if a mistake is made, it affects the decision process. People tend to ask friends or family for reassurance or spend time interacting with third-party experts to get a second opinion.
Patients want to share their health records with their circle of trust: family, close friends, doctors, etc. Insurance policyholders would love to be able to conveniently and securely share access to the policy terms with the beneficiaries or with those insured.
Modern access control platforms can apply the same relationship principle for group accounts or family accounts. You can authorize users to manage access for their family or team and easily add or remove people within the conditions set by your company policy.
You Are What You Like
And without getting too technical, here’s where we make the difference. A family account at, let’s say, Netflix, is not actually a set of individuals but a set of playlists. Your partner or daughter that you see on the screen is in fact a representation of a particular playlist. They get recommendations based on the items in their playlist.
So, Netflix and most other broadcasters or publishing companies view a group subscription as a collection of playlists, not of actual individuals.
We take a different approach. Relationship-based access control views every user as an individual who needs to first sign up to get access. You can control fraud or freeloading much better with individuals than with profiles because you no longer need to offer or detect concurrent viewership. Each person gets individual access.
And you can use these relationships to make recommendations (e.g. the person who I invited to get access to that article might like the other articles that I’m reading now).
Authorization Technology for Consumers
And here’s another thing — modern access control solutions let organizations build access policies with more attributes than what is currently available, especially in the consumer space (access management was originally conceived for the business environment).
To give an example, a media company can build a rule that states, “Premium subscribers can share 5 technology articles per month with friends, who then get full access to all technology articles from ‘title X for the next 2 weeks, as long as they access it from within the same country as the subscriber.”
Authorization management has evolved to meet consumer sharing expectations and habits that they have acquired through social media while ensuring security and privacy. Advanced access technology can contribute to a strategy that’s based on empowering your customer and with it comes to a required change in how you build and nurture relationships with potential and existing customers.
Most companies do not have all of the components in place to claim they are customer-centric, but the most important part to remember is this: Customer-centricity starts by focusing on how customers want to interact with you. You only get one chance to make a good first impression, and yours may be in the hands of advanced access management.
Other Whitepapers

The Developer’s Guide to Relationship-based Access Control
Start implementing Relationship-based access control. Your databases likely contain a network of entities and their relationships already.
Whitepapers
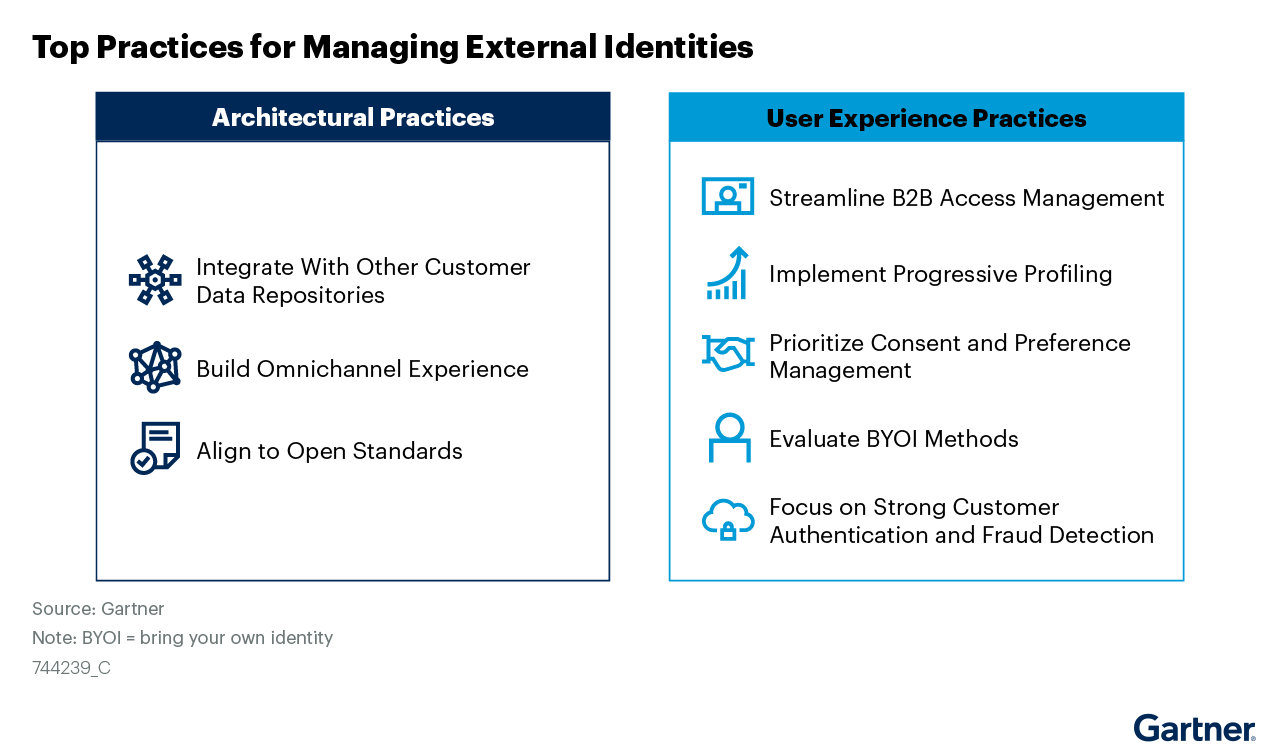
Managing External Identities Using a Customer Identity and Access Management Tool
Use this Gartner® research to learn how to implement a cohesive customer access management solution that lets customers, partners, and gig workers access your applications.
Whitepapers

Nine Common Access Management Misconceptions Debunked
It’s about time to clear up some common misconceptions about access management. Here’s a list of the traditional views that no longer hold true.
Whitepapers

How authorization technology will revolutionize the way we collaborate
Advanced access control systems let stakeholders, both inside and outside the organization, conveniently share information, knowledge and functionalities.
Whitepapers

Monetize a Loyal Audience without Alienating more Casual Viewers who want to Sample Content
How publishers & broadcasters use advanced CIAM technology to grow and engage audiences and convert casual viewers.
Whitepapers

Scaled Access ROI
Whether you want to replace a homegrown solution or an existing vendor, the investment you make in us will be a good one.
Whitepapers

Accelerating Secure OAuth 2.0 Compliant Advanced Authorization: Authlete & Scaled Access
Read how Authlete and Scaled Access’s combined solution enables organizations to build and operate OAuth 2.0 compliant authorization servers
Whitepapers

Data Protection:
From Obligation to Opportunity
GDPR leverages significant opportunities in terms of engagement and customer retention.
Whitepapers

10 Reasons to Buy an Access Management Tool Rather Than Build
Think cost is the important factor? Think again.
Whitepapers

Sharing Confidential Data Doesn’t Require Sharing Credentials
Read how advanced authorization platforms provide an alternative to credential sharing.

