Users want to give others access to your applications, resources or services.
Let them.
#1 platform for advanced access management
The only solution that lets you authorize users to gain and grant access securely.
Relationship-based permissions
Empower your users to offer access through frictionless sharing and next-generation delegated administration.
Externalized authorization
Orchestrate authorization policies across different applications, systems, and services, which delivers better audit and compliance results.
Consent lifecycle management
We request informed consent each time you collect new data from your users or update your terms.
REST API integration
We seamlessly integrate with your architecture and existing identity management solution using OAuth 2.0 and OIDC 1.0 standards.
There’s a better way to grant access
to your services or systems.
We built it.
Scaled Access enriches your identity solution with an access solution that takes relationships into account. You can start defining access policies that specify which interpersonal relationships can share or grant access.
Our graphical policy editor and dynamic authorization take the pain and stress away from building these policies.
Digital Ecosystem Access
Authorize employees, partners, and customers to manage access to all your services, applications, or enterprise systems for their staff and the extended workforce.
Consumer Access
Enable secure sharing of subscriptions, protected content, or personal information with friends, family, or group members.
Scaled Access is built to scale
30
MILLION
USERS
5
MILLISECONDS
AUTHORIZATION
1.2X TO 10X
USER BASE
GROWTH


Scaled Access has helped us drive customer engagement
Antoine Frack Head of Smart & Connected (Digital Factory)
and enhance our reputation.
Explore more
-
OneWelcome continues growth strategy with the acquisition of Scaled Access
![]()
Identity and Access Management platform OneWelcome expands with Scaled Access’ fine-grained and policy-based access
-
The Developer’s Guide to Relationship-based Access Control
![]()
Start implementing Relationship-based access control. Your databases likely contain a network of entities and their relationships already.
-
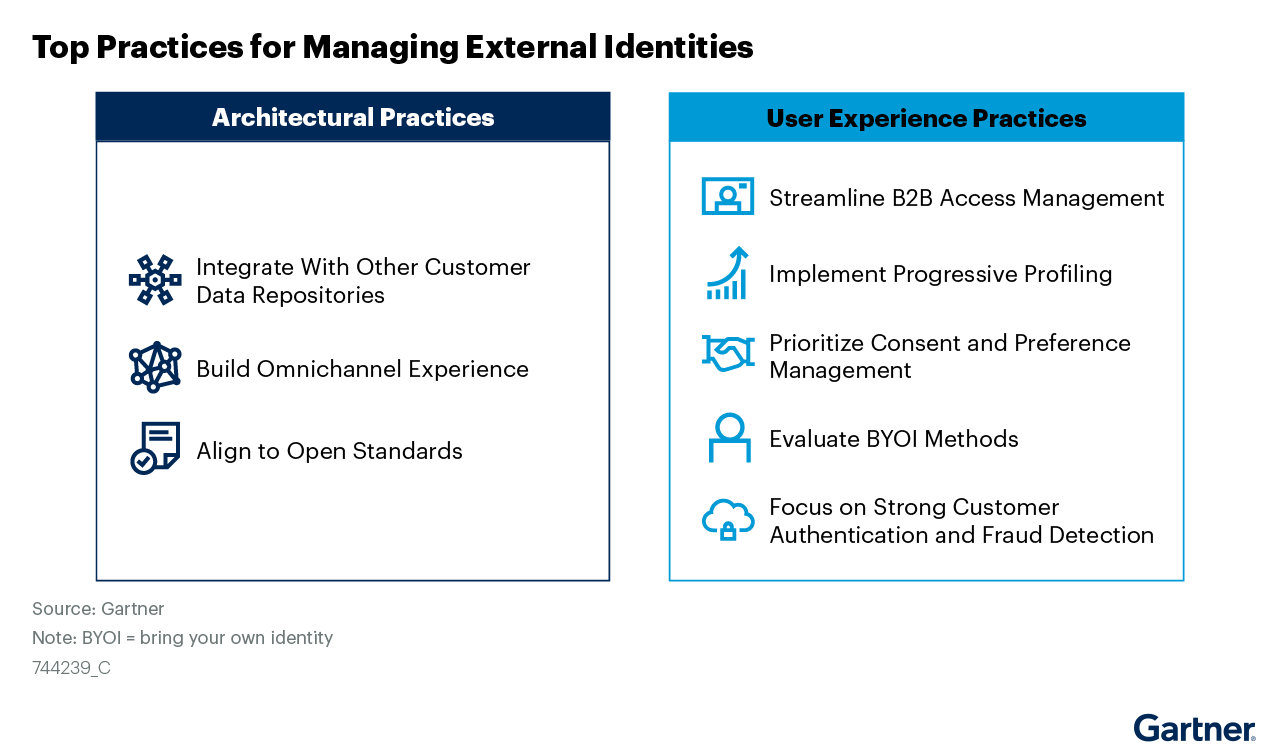
Managing External Identities Using a Customer Identity and Access Management Tool
![]()
Use this Gartner® research to learn how to implement a cohesive customer access management solution that lets customers, partners, and gig workers access your applications.
Ready to adapt to how your users interact in the real world?